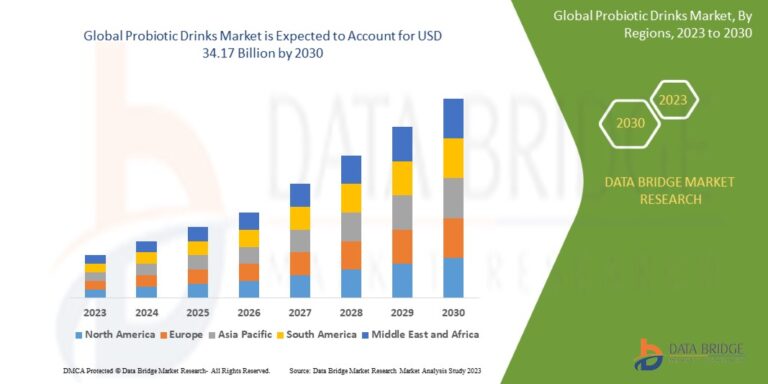
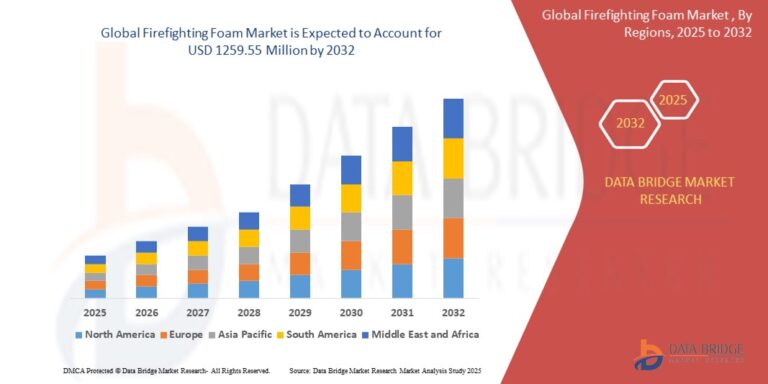
In today’s interconnected world, web applications are the backbone of businesses across industries. From e-commerce platforms and customer portals to SaaS products and online services, these applications hold valuable data and serve as the first touchpoint for customers. But this also makes them a prime target for cybercriminals.
This is why Web Application Security has become one of the most crucial aspects of modern cybersecurity. Without it, organizations face risks such as data breaches, financial losses, compliance violations, and irreparable reputational damage.
What Is Web Application Security?
Web Application Security refers to the processes, technologies, and best practices used to protect web applications from cyber threats. It ensures that applications can resist attacks such as injection flaws, cross-site scripting, broken authentication, data exposure, and more.
In short, it’s about protecting the integrity, confidentiality, and availability of applications that interact with users and handle sensitive business data.
Why Web Application Security Is Essential
- Web apps are the top attack target
Reports consistently show that nearly half of all cyberattacks are aimed at web applications, making them a primary focus for malicious actors. - Customer trust depends on security
A single vulnerability can expose sensitive customer data, damaging brand reputation and customer confidence. - Regulatory compliance
Standards like GDPR, HIPAA, and PCI DSS require organizations to secure digital assets, including web applications. Failure to comply can lead to heavy penalties. - Business continuity
Attacks can cause downtime, disrupt services, and directly affect revenue streams.
By prioritizing web application security, businesses not only protect themselves but also build trust with customers and partners.
How Web Application Security Testing Works
Professional Web Application Security testing involves a combination of automated tools and manual assessments. Here’s how the process generally unfolds:
1. Vulnerability Scanning
Security experts use industry-standard tools to identify common vulnerabilities such as cross-site scripting (XSS), SQL injection, insecure configurations, and outdated components.
2. Manual Penetration Testing
Automated tools cannot identify complex business logic flaws or chained vulnerabilities. Skilled testers replicate real-world attack scenarios to uncover deeper issues that scanners may miss.
3. Multi-Mode Testing
Security assessments often combine:
- White Box Testing – with full access to source code and architecture to identify internal flaws.
- Grey Box Testing – simulating attackers with limited insider knowledge.
- Black Box Testing – assessing what an external hacker without prior knowledge could exploit.
4. Detailed Reporting
Organizations receive a comprehensive report detailing:
- Identified vulnerabilities
- Business and technical impact
- Risk categorization (critical, high, medium, low)
- Recommended remediation steps
5. Remediation & Re-Testing
After developers fix vulnerabilities, security teams re-test to validate that issues have been resolved and no new flaws were introduced.
Common Vulnerabilities in Web Applications
Web Application Security testing primarily targets the most common attack surfaces, many of which are outlined in the OWASP Top 10. These include:
- Injection flaws (SQL, NoSQL, OS commands)
- Broken authentication leading to account takeover
- Sensitive data exposure through weak cryptography
- Cross-site scripting (XSS) allowing attackers to inject malicious scripts
- Broken access controls enabling privilege escalation
- Insecure deserialization opening the door to remote code execution
- Security misconfigurations due to poor server or application setups
- Use of vulnerable third-party components
- Insufficient logging and monitoring that delay attack detection
Beyond these, testers also look for business logic flaws and unique vulnerabilities specific to how an application is designed.
Benefits of Professional Web Application Security
1. Proactive Threat Mitigation
Security testing identifies weaknesses before attackers can exploit them, reducing the risk of breaches.
2. Cost Savings
Fixing vulnerabilities early is far cheaper than dealing with data breaches, lawsuits, and reputational damage.
3. Stronger Compliance Posture
Regular security assessments help organizations meet regulatory requirements and industry standards.
4. Customer Trust & Confidence
Demonstrating a commitment to security reassures customers that their data is safe.
5. Long-Term Resilience
By embedding security into the application development lifecycle, businesses create sustainable defenses against evolving threats.
SecureRoot’s Approach to Web Application Security
At SecureRoot, Web Application Security testing is a core component of our Vulnerability Assessment and Penetration Testing (VAPT) services. We use a hybrid approach that combines automation, manual assessments, and tailored methodologies for maximum coverage.
Key Highlights of Our Approach:
- Comprehensive methodology blending white, grey, and black box testing.
- Use of trusted tools alongside manual analysis to uncover both common and complex vulnerabilities.
- Focus on business impact to help prioritize remediation based on actual risks.
- Actionable reports designed for both technical teams and executive decision-makers.
- Continuous support to assist in remediation and future security enhancements.
Best Practices for Stronger Web Application Security
Beyond professional testing, organizations should adopt ongoing practices to improve security:
- Secure Development Lifecycle (SDLC) – Integrate security into every phase of development, from design to deployment.
- Regular Security Training – Ensure developers and employees understand secure coding and cyber hygiene.
- Patch Management – Keep all software, frameworks, and libraries updated.
- Strong Authentication & Authorization – Implement multi-factor authentication and enforce least-privilege access.
- Data Encryption – Encrypt sensitive data both in transit and at rest.
- Regular Penetration Testing – Schedule periodic testing to stay ahead of evolving threats.
- Incident Response Plan – Prepare for potential breaches with clear protocols to minimize damage.
Why Choose SecureRoot for Web Application Security?
- Expertise – A team of certified security professionals with years of experience across industries.
- Tailored Testing – Every engagement is customized to fit your application architecture and business risks.
- Comprehensive Coverage – From technical flaws to logic vulnerabilities, we uncover what others might miss.
- Practical Insights – Reports that go beyond technical jargon, offering actionable steps aligned with business objectives.
- Long-Term Partnership – Ongoing support to maintain resilience against new and emerging cyber threats.
Final Thoughts
In today’s digital-first world, securing your web applications is no longer optional, it’s a business necessity. Web Application Security protects not just data but also customer trust, brand reputation, and overall business continuity.
By investing in proactive security testing and best practices, organizations can stay ahead of attackers, comply with regulations, and foster customer confidence. SecureRoot’s proven expertise and comprehensive methodologies ensure that your applications remain strong, resilient, and secure against the ever-evolving cyber threat landscape.